Understanding the SSL/TLS Handshake Process
Daniel MartinezShare
When you visit a secure website protected by SSL Certificates, an intricate process begins behind the scenes before any data transmission occurs.
This critical process is known as the SSL/TLS handshake, and it forms the foundation of all secure communication on the internet. Understanding how this handshake works is essential for system administrators, web developers, and anyone responsible for implementing SSL Certificate security.
The SSL/TLS handshake is a sophisticated protocol that establishes a secure connection between a client (typically a web browser) and a server.
This process ensures that all data transmitted between these parties remains encrypted and protected from potential eavesdropping or tampering.
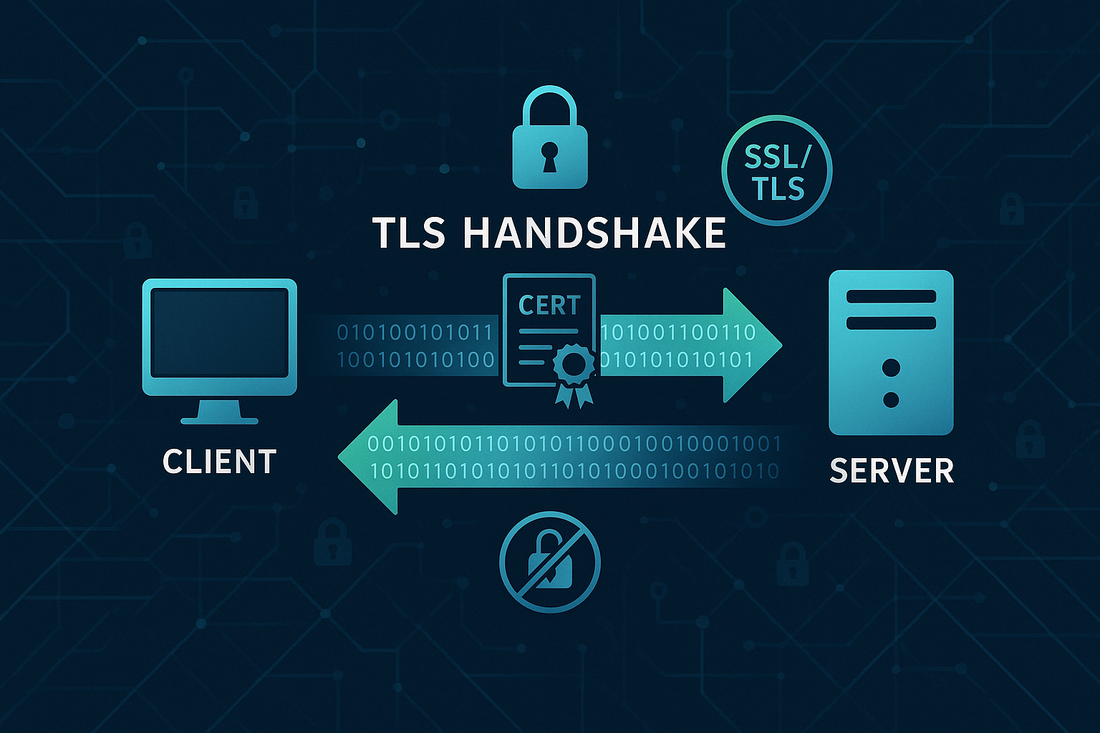
What Is the SSL/TLS Handshake Process?
The SSL/TLS handshake represents the initial negotiation phase between a client and server when establishing a secure connection.
This process involves multiple steps where both parties authenticate each other, agree on encryption methods, and establish the cryptographic keys that will be used for the duration of the session. Think of it as a formal introduction and agreement process that must be completed before any sensitive information can be safely transmitted.
During this handshake, several critical functions are performed.
These include identity verification through SSL Certificate validation, cipher suite negotiation, protocol version agreement, and symmetric key generation. The entire process typically takes just a few milliseconds, but the security it provides is invaluable.
The handshake uses a combination of asymmetric and symmetric encryption.
Initially, asymmetric encryption (using Public and Private Key pairs) is employed for secure key exchange and authentication. Once the handshake is complete, symmetric encryption takes over for the actual data transmission, as it is much faster and more efficient for large amounts of data.
The Step-by-Step SSL/TLS Handshake Process
The SSL/TLS handshake consists of several distinct phases, each serving a specific purpose in establishing secure communication.
Step one begins with the Client Hello message.
When a client initiates a connection to a server protected by an SSL Certificate, it sends a Client Hello message containing the highest SSL/TLS protocol version the client supports, a randomly generated number for later use, a list of cipher suites the client can work with, and any SSL Certificate extensions the client supports.
The server responds with a Server Hello message.
This includes the SSL/TLS protocol version selected from the client's supported versions, another randomly generated number from the server side, the cipher suite chosen from the client's list, and the session ID for this particular connection. This negotiation ensures both parties use compatible encryption methods and protocol versions.
Next comes the SSL Certificate presentation phase.
The server sends its SSL Certificate to the client, which contains the server's Public Key, the server identity information, and the digital signature from the Certificate Authority (CA).
SSL Certificate Validation and Authentication
Once the client receives the SSL Certificate from the server, it must verify the SSL Certificate's authenticity and validity.
This verification process involves several checks. The client verifies that the SSL Certificate was issued by a trusted Certificate Authority (CA), confirms that the SSL Certificate has not expired, checks that the SSL Certificate has not been revoked, and ensures that the Common Name (CN) or Subject Alternative Name (SAN) matches the server domain.
If SSL Certificate validation fails at any point, the handshake process terminates.
The client will display a security warning to the user. This is why choosing a reputable SSL Certificate provider is crucial for maintaining seamless user experiences and avoiding security warnings that can drive visitors away.
Key Exchange and Pre-Master Secret Generation
After successful SSL Certificate validation, the key exchange phase begins.
The client generates a pre-master secret, which is a random value used to create the symmetric encryption keys for the session. This pre-master secret is encrypted using the server's Public Key from the SSL Certificate and sent to the server. Only the server, possessing the corresponding Private Key, can decrypt this pre-master secret.
The security of this phase depends entirely on the strength of the SSL Certificate key pair.
Modern SSL Certificates support various key lengths, including 2048-bit RSA keys and ECC keys, providing robust security for the key exchange process. The choice of key type and length impacts both security levels and performance.
Both client and server now possess the same pre-master secret and the two random numbers exchanged earlier.
Using a predetermined algorithm, both parties independently generate the same set of symmetric encryption keys from these shared values. This ensures both parties have identical keys without ever transmitting the actual symmetric keys across the network.
Session Key Derivation and Cipher Activation
The final phase of the handshake involves deriving session keys and activating the chosen cipher suite.
Using the pre-master secret and random values exchanged earlier, both client and server generate several keys : a client write key for encrypting data sent from client to server, a server write key for encrypting data sent from server to client, and initialization vectors for certain cipher modes.
Once these keys are generated, both parties send a Change Cipher Spec message.
This indicates that all subsequent communication will be encrypted using the newly established keys. This is followed by a Finished message from both sides, which is the first message encrypted with the new session keys. This message contains a hash of all previous handshake messages, allowing each party to verify that the handshake completed successfully without tampering.
Different Types of SSL/TLS Handshakes
Not all SSL/TLS handshakes are identical.
The process can vary depending on the SSL Certificate type, the cipher suite selected, and whether session resumption is being used.
Full handshakes occur when a client connects to a server for the first time or when session resumption is not available.
This involves all the steps described above and typically takes several round trips between client and server. Abbreviated handshakes happen when session resumption is used, allowing clients to reconnect using previously established session parameters, significantly reducing connection time.
SSL Certificates support both full and abbreviated handshakes.
Modern SSL Certificates are designed with advanced features that support handshake optimizations like TLS 1.3, which reduces the number of round trips required for establishing secure connections.
TLS 1.3 Handshake Improvements
The latest version of the TLS protocol, TLS 1.3, introduces significant improvements to the handshake process.
These enhancements reduce latency, improve security, and simplify the overall process. TLS 1.3 handshakes require fewer round trips between client and server, often establishing secure connections in just one round trip compared to the two or three required by earlier versions.
TLS 1.3 eliminates support for older, less secure cipher suites and implements perfect forward secrecy by default.
This means that even if a server's Private Key is compromised in the future, previously recorded encrypted traffic cannot be decrypted. Modern SSL Certificates fully support TLS 1.3, ensuring websites and applications can take advantage of these improvements.
The simplified TLS 1.3 handshake also reduces the attack surface.
It eliminates unnecessary complexity and potential vulnerabilities present in earlier protocol versions. SSL Certificates with TLS 1.3 support benefit from these security enhancements while maintaining compatibility with older systems.
Common Handshake Issues and Troubleshooting
Despite the robustness of the SSL/TLS handshake process, various issues can prevent successful connection establishment.
Common issues include SSL Certificate validation failures, cipher suite mismatches, protocol version incompatibilities, and network connectivity problems.
SSL Certificate validation failures are among the most frequent handshake issues.
These can occur due to expired SSL Certificates, incorrect SSL Certificate chains, domain name mismatches, or SSL Certificates from untrusted authorities. Proper SSL Certificate chain construction and accurate domain validation help minimize these issues.
Cipher suite mismatches happen when client and server cannot agree on a common encryption method.
This typically occurs when one party only supports outdated cipher suites while the other requires modern, secure options. Modern SSL Certificates support a wide range of cipher suites, ensuring compatibility with both legacy systems and current security requirements.
Performance Optimization for SSL/TLS Handshakes
While security is the primary concern, handshake performance significantly impacts user experience.
Slow handshakes can increase page load times and create frustrating delays for website visitors. Several optimization techniques can improve handshake performance without compromising security.
Session resumption is one of the most effective optimization techniques.
By caching session parameters, clients can reconnect to servers using abbreviated handshakes that require fewer computational resources and network round trips. SSL Certificates support various session resumption mechanisms, including session IDs and session tickets.
SSL Certificate chain optimization is another important factor.
Shorter SSL Certificate chains reduce the amount of data transmitted during the handshake, while proper intermediate SSL Certificate configuration ensures clients can build complete trust paths to root authorities.
Security Considerations and Best Practices
The SSL/TLS handshake process requires proper implementation and configuration to maintain security.
Several best practices should be followed when deploying SSL Certificates to ensure maximum protection against various attack vectors.
Always use the latest supported TLS version while maintaining compatibility with legitimate clients.
Disable support for obsolete protocols like SSL 2.0 and SSL 3.0, which contain known vulnerabilities. Configure cipher suites to prefer modern, secure options while avoiding weak or deprecated algorithms.
Regular SSL Certificate renewal and monitoring are essential for maintaining security.
Expired SSL Certificates cause handshake failures and security warnings, potentially driving users away from your website. Trustico® offers SSL Certificate monitoring services and renewal reminders to help prevent expiration issues.
Choosing the Right SSL Certificate for Optimal Performance
Different types of SSL Certificates can impact handshake performance and security in various ways.
Domain Validation (DV) SSL Certificates typically have the fastest issuance times and simplest validation requirements, making them ideal for basic encryption needs. Organization Validation (OV) and Extended Validation (EV) SSL Certificates provide additional identity verification.
Wildcard and Multi Domain SSL Certificates can impact handshake performance.
These SSL Certificate types allow you to secure multiple domains or subdomains with a single SSL Certificate, simplifying management while maintaining security. Trustico® offers various SSL Certificate options to meet different organizational needs.
Future of SSL/TLS Handshake Technology
The SSL/TLS handshake process continues to evolve with new technologies and security requirements.
Emerging trends include post-quantum cryptography preparation, enhanced privacy features, and further performance optimizations.
Post-quantum cryptography represents a significant future consideration.
Quantum computers may eventually be capable of breaking current public key cryptographic systems. Research is ongoing into quantum-resistant algorithms that could be integrated into future TLS versions.
Enhanced privacy features aim to protect even more information during the handshake process.
Encrypted Client Hello (ECH) prevents network observers from determining which specific websites users are visiting, even when monitoring encrypted traffic. As these technologies mature, SSL Certificates will support them to provide maximum privacy protection.
Understanding SSL/TLS Handshake Fundamentals
Understanding the SSL/TLS handshake process is crucial for anyone responsible for web security.
The handshake process may seem complex, but with properly configured SSL Certificates, it becomes a seamless and highly secure method for establishing encrypted communications.
SSL Certificates optimize every aspect of the handshake process, from initial client hello messages to final cipher activation.
Trustico® provides comprehensive SSL Certificate options to ensure you can find the right solution for your specific security and performance requirements, backed by industry-leading security standards and expert technical support.



